Using Openssh
So I am past the point of getting OpenSSH server to run. I have disabled password ssh login and only use keys. Once you click connect, your VNC client will use the encrypted SSH tunnel and make the connection between local and remote machines on port 5901. You should then be able to work on the remote. Using the OpenSSH Beta in Windows 10 Fall Creators Update and Windows Server 1709. SSH Isn’t Even a Thing. The one I will discuss in this article is SSH, a secure remote protocol which is used to work remotely on other machines or transfer data between computers. Installing and Using the OpenSSH Utilities. Installation of the OpenSSH utilities can only be performed by your Unix systems administrator, and is.
Most UNIX-like operating systems include the OpenSSH project’s SSH client and server software. It’s relatively straightforward to configure the OpenSSH server for a range of usecases. In this post we’ll do the following:
Create a system group
exchangefiles.Create a
/home/exchangefiles/directory andfiles/directory within it.Allow users in the
exchangefilesgroup to connect to the server using SFTP (but not SSH).Lock users in the
exchangefilesgroup into the/home/exchangefiles/directory using a chroot.Restrict some other options for users in the
exchangefilesgroup.
So we’ll allow these users to connect to the SSH server and use SFTP to access a specific directory, and nothing else.
Preparations
First, lets create the new group:
Then create the new directories:
SSHD configuration
The OpenSSH server configuration is typically called something like /etc/ssh/sshd_config. Find this file and open it in an editor. First we’ll make sure it will support SFTP in a chrooted environment. Search for a existing Subsystem sftp statement or insert it if it’s missing:
Here internal-sftp means “use the SFTP server built into sshd”. The default on many platforms is to use an external SFTP implementation (/usr/libexec/sftp-server on Mac OS X or /usr/libexec/openssh/sftp-server on RedHat-y Linux distros) but this won’t exist inside the chroot. (Previous versions of this post omitted discussion of Subsystem; thanks to Matthew Saltzman for suggesting the improvement.)
Next we’re going to add a section to the end of the file using the Match directive which applies to users in our group:
After that we specify the configuration directives which apply the matched connections:
Let’s lock down some of the additional capabilities of the OpenSSH server so these people can’t, e.g., forward connections through the server and into our private network:
So the whole block looks like this:
Testing
To apply the configuration change, just restart your SSH server, create a user and try to access the site.
Connecting with sftp should result in a connection, but ssh should return an error message:
This service allows sftp connections only.
Connection to server.example.com closed.
When connected you should be able to list, upload and delete files under /files/.
TODO
If you’re doing something like this, you probably want the users to be able to access each other’s files – otherwise why bother sharing a space? To do this you’ll need to set the umask so that files are created with the correct permissions.
The internal-sftp command has a -u option which might help, but I haven’t tested this.
Updates
- 2015-01-08: Tweaked group write permissions on
/home/exchangefilesafter feedback from “Nik”. Thanks Nik!
Table of Contents
Introduction


SSH can handle authentication using a traditional username and password combination or by using a public and private key pair. The SSH key pair establishes trust between the client and server, thereby removing the need for a password during authentication. While not required, the SSH private key can be encrypted with a passphrase for added security.
The PuTTY SSH client for Microsoft Windows does not share the same key format as the OpenSSH client. Therefore, it is necessary to create a new SSH public and private key using the PuTTYgen tool or convert an existing OpenSSH private key.
Requirements
Using Openssh Server Windows 10
- PuTTY SSH client for Microsoft Windows
- Remote server accessible over OpenSSH
Install PuTTY and PuTTYgen
Both PuTTY and PuTTYgen are required to convert OpenSSH keys and to connect to the server over SSH. These two tools can be downloaded individually or, preferably, as a Windows installer from the PuTTY Download Page.
Once the PuTTY Windows installer is downloaded, double-click the executable in the Download folder and follow the installation wizard. The default settings are suitable for most installations. Both PuTTY and PuTTYgen should now be accessible from the Windows Programs list.
Use Existing Public and Private Keys
If you have an existing OpenSSH public and private key, copy the id_rsa key to your Windows desktop. This can be done by copying and pasting the contents of the file or using an SCP client such as PSCP which is supplied with the PuTTY install or FileZilla.
Next launch PuTTYgen from the Windows Programs list.
- Click
Conversionsfrom the PuTTY Key Generator menu and selectImport key. - Navigate to the OpenSSH private key and click
Open. - Under
Actions/Save the generated key, selectSave private key. - Choose an optional passphrase to protect the private key.
- Save the private key to the desktop as
id_rsa.ppk.
If the public key is already appended to the authorized_keys file on the remote SSH server, then proceed to Connect to Server with Private Key.
Otherwise, proceed to Copy Public Key to Server.
Create New Public and Private Keys

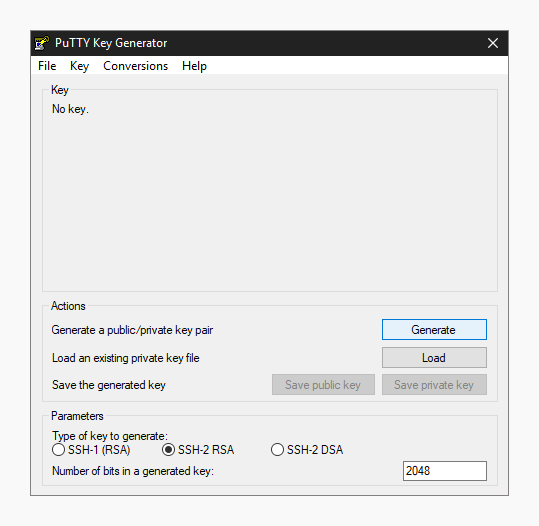
Launch PuTTYgen from the Windows Programs list and proceed with the following steps.
- Under
Parameters, increase theNumber of bits in a generated key:to a minimum value of 2048. - Under
Actions/Generate a public/private key pair, clickGenerate. - You will be instructed to move the mouse cursor around within the PuTTY Key Generator window as a randomizer to generate the private key.
- Once the key information appears, click
Save private keyunderActions/Save the generated key. - Save the private key to the desktop as
id_rsa.ppk. - The box under
Key/Public key for pasting into OpenSSH authorized_keys file:contains the public key.
Copy Public Key to Server
The OpenSSH public key is located in the box under Key / Public key for pasting info OpenSSH authorized_keys file:. The public key begins with ssh-rsa followed by a string of characters.
- Highlight entire public key within the PuTTY Key Generator and copy the text.
- Launch PuTTY and log into the remote server with your existing user credentials.
Use your preferred text editor to create and/or open the
authorized_keysfile:Paste the public key into the
authorized_keysfile.Save the file and close the text editor.
Adjust the permissions of the
authorized_keysfile so that the file does not allow group writable permissions.Logout of the remote server.
Connect to Server with Private Key
Download Openssh
Now it is time to test SSH key authentication. The PuTTYgen tool can be closed and PuTTY launched again.
Using Openssh On Windows
- Enter the remote server Host Name or IP address under
Session. - Navigate to
Connection>SSH>Auth. - Click
Browse...underAuthentication parameters/Private key file for authentication. - Locate the
id_rsa.ppkprivate key and clickOpen. - Finally, click
Openagain to log into the remote server with key pair authentication.
